What is Access Control

A Brief History
The original access control system was a guard posted in front of a structure. The earliest known lock and key device dates back to 4,000 B.C. It was discovered in the ruins of Nineveh in modern day Iraq. The lock and key solution became an incredible convenience, but was originally made of wood. These locks were easily picked and skeleton keys would work on many different locks. Robert Barron patented a double-acting lever tumbler lock in 1778. In 1784, Joseph Bramah patented a high-security lock that’s still manufactured and sold in London today.
Locks have come a long way since the eighteenth century. The future of locks lies in integrated technology networks, which controlled access systems already employ. In 2015, Yale and Schlage launched a smartlocks that interact with your smartphone. According to Whitney Fay of Locknet:
Your smart phone will now hold your smart lock’s virtual key. With the August Smart Lock, for instance, you have the capability to create virtual keys and then send them electronically to everyone who needs access. You can then go in and set the amount of time you want each key to be active. Currently, smart locks are only used in the hospitality industry and in private homes, but the technology is sure to make its way to the commercial market in the near future.
The first access control systems used PIN numbers and key cards that used magnetic strips. These were upgraded in the 1970s to proximity cards or RFID (radio-frequency identification) technology. While PIN numbers and proxy cards are still a viable option, the future of controlled access is in biometric technology.
How It Works

When the correct PIN or RFID indicator is received, the reader sends a signal to a programmed door controller. The controller must be programmed to recognize new signals or to forget signals that are no longer needed. When the controller receives the signal it then releases an electric lock for the specific door. After the individual who triggered the door pass through it and closes the door the lock reengages.
There are two different styles of cards: active and passive. Passive cards are more common than active cards. They are powered by radio frequency signals sent from the reader device. There is a limited range. Contactless smartcards can be used in controlled access and has gained new traction in contactless payment systems. These cards consist of an internal antenna, capacitor, and integrated circuit. There is a user ID specific to the card, which is programmed into the circuit.
Active cards are also known as vicinity cards and are powered by a lithium battery. They have a wider range than passive cards. These can be excellent solutions for parking area control because the device can be put into an authorized car and the gate will open as the car approaches. The integrated circuit contains a receiver which amplifies the signal from the reader. There is a transmitter circuit in the chip that transmits a stronger return signal.
Basic Components of an Access Control System
There are some basic components to an access control system.
The Brain
The software and server that power the whole system is responsible for recording system activity, and relaying data to and from the intelligent controllers. The server is usually a standard computer with firewall protections.
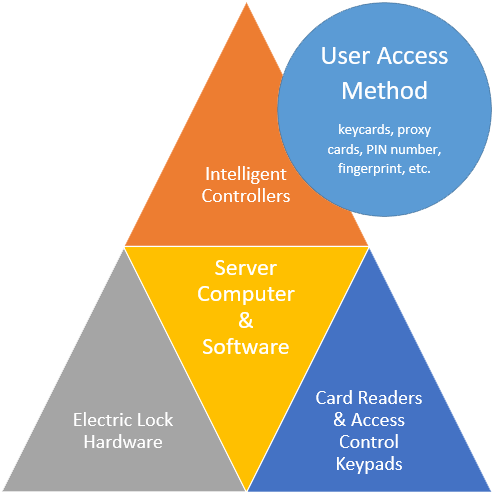
The Field Panels
Reader devices, electric lock hardware, and other access control devices are connected to the field panels. The number of panels is determined by the size of the system. These are usually stored in the communications closet.
Lock Hardware
Electric locks, strikes, exit devices are necessary for the system. Electromagnetic locks or other versions of the locking mechanism are determined by the door or system design. The fire code restricts lock hardware from ever preventing anyone from leaving the building.
Keypads and Readers
There are many options for the device that reads the user ID. Keypads and readers can be separate or combined. PIN numbers can be a back-up to a card or fingerprint, but weaken the security of the system since PIN numbers can be leaked to unauthorized individuals. Keypads alone can be an appropriate solution for smaller systems. There are two types of readers: insertion type and proximity. The reader type will determine the type of access card.
User IDs
User IDs must be stored into the software and at least one device that can communicate with the reader. Keycards and proximity cards are physical devices do not necessarily look like an ID or credit card, but there are many that do. Some access devices are small and can be attached to a keychain or put inside a wallet. A user ID can be a simple PIN number or a fingerprint if it is a biometric system. Retina scanners and voice recognition readers are additional biometric options.
A Note on Biometrics
While the future of controlled access is going to involve biometrics, the technology is still being developed. There were issues with biometric technologies, but in recent years there have been great strides made to improve the technology. Imagine eliminating the expense of keys and keycards in favor of a fingerprint. Biometric systems will offer the highest level of security.
Learn More